Section 21.9: Cytotoxic T Cells and Superantigens
- Page ID
- 146456
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\( \newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\)
( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\id}{\mathrm{id}}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\kernel}{\mathrm{null}\,}\)
\( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\)
\( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\)
\( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\AA}{\unicode[.8,0]{x212B}}\)
\( \newcommand{\vectorA}[1]{\vec{#1}} % arrow\)
\( \newcommand{\vectorAt}[1]{\vec{\text{#1}}} % arrow\)
\( \newcommand{\vectorB}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vectorC}[1]{\textbf{#1}} \)
\( \newcommand{\vectorD}[1]{\overrightarrow{#1}} \)
\( \newcommand{\vectorDt}[1]{\overrightarrow{\text{#1}}} \)
\( \newcommand{\vectE}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash{\mathbf {#1}}}} \)
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\(\newcommand{\avec}{\mathbf a}\) \(\newcommand{\bvec}{\mathbf b}\) \(\newcommand{\cvec}{\mathbf c}\) \(\newcommand{\dvec}{\mathbf d}\) \(\newcommand{\dtil}{\widetilde{\mathbf d}}\) \(\newcommand{\evec}{\mathbf e}\) \(\newcommand{\fvec}{\mathbf f}\) \(\newcommand{\nvec}{\mathbf n}\) \(\newcommand{\pvec}{\mathbf p}\) \(\newcommand{\qvec}{\mathbf q}\) \(\newcommand{\svec}{\mathbf s}\) \(\newcommand{\tvec}{\mathbf t}\) \(\newcommand{\uvec}{\mathbf u}\) \(\newcommand{\vvec}{\mathbf v}\) \(\newcommand{\wvec}{\mathbf w}\) \(\newcommand{\xvec}{\mathbf x}\) \(\newcommand{\yvec}{\mathbf y}\) \(\newcommand{\zvec}{\mathbf z}\) \(\newcommand{\rvec}{\mathbf r}\) \(\newcommand{\mvec}{\mathbf m}\) \(\newcommand{\zerovec}{\mathbf 0}\) \(\newcommand{\onevec}{\mathbf 1}\) \(\newcommand{\real}{\mathbb R}\) \(\newcommand{\twovec}[2]{\left[\begin{array}{r}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\ctwovec}[2]{\left[\begin{array}{c}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\threevec}[3]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\cthreevec}[3]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\fourvec}[4]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\cfourvec}[4]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\fivevec}[5]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\cfivevec}[5]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\mattwo}[4]{\left[\begin{array}{rr}#1 \amp #2 \\ #3 \amp #4 \\ \end{array}\right]}\) \(\newcommand{\laspan}[1]{\text{Span}\{#1\}}\) \(\newcommand{\bcal}{\cal B}\) \(\newcommand{\ccal}{\cal C}\) \(\newcommand{\scal}{\cal S}\) \(\newcommand{\wcal}{\cal W}\) \(\newcommand{\ecal}{\cal E}\) \(\newcommand{\coords}[2]{\left\{#1\right\}_{#2}}\) \(\newcommand{\gray}[1]{\color{gray}{#1}}\) \(\newcommand{\lgray}[1]{\color{lightgray}{#1}}\) \(\newcommand{\rank}{\operatorname{rank}}\) \(\newcommand{\row}{\text{Row}}\) \(\newcommand{\col}{\text{Col}}\) \(\renewcommand{\row}{\text{Row}}\) \(\newcommand{\nul}{\text{Nul}}\) \(\newcommand{\var}{\text{Var}}\) \(\newcommand{\corr}{\text{corr}}\) \(\newcommand{\len}[1]{\left|#1\right|}\) \(\newcommand{\bbar}{\overline{\bvec}}\) \(\newcommand{\bhat}{\widehat{\bvec}}\) \(\newcommand{\bperp}{\bvec^\perp}\) \(\newcommand{\xhat}{\widehat{\xvec}}\) \(\newcommand{\vhat}{\widehat{\vvec}}\) \(\newcommand{\uhat}{\widehat{\uvec}}\) \(\newcommand{\what}{\widehat{\wvec}}\) \(\newcommand{\Sighat}{\widehat{\Sigma}}\) \(\newcommand{\lt}{<}\) \(\newcommand{\gt}{>}\) \(\newcommand{\amp}{&}\) \(\definecolor{fillinmathshade}{gray}{0.9}\)Activation and Differentiation of Cytotoxic T Cells
Cytotoxic T cells (also referred to as cytotoxic T lymphocytes, or CTLs) are activated by APCs in a three-step process similar to that of helper T cells. The key difference is that the activation of cytotoxic T cells involves recognition of an antigen presented with MHC I (as opposed to MHC II) and interaction of CD8 (as opposed to CD4) with the receptor complex. After the successful co-recognition of foreign epitope and self-antigen, the production of cytokines by the APC and the cytotoxic T cell activate clonal proliferation and differentiation. Activated cytotoxic T cells can differentiate into effector cytotoxic T cells that target pathogens for destruction or memory cells that are ready to respond to subsequent exposures.
As noted, proliferation and differentiation of cytotoxic T cells is also stimulated by cytokines secreted from TH1 cells activated by the same foreign epitope. The co-stimulation that comes from these TH1 cells is provided by secreted cytokines. Although it is possible for activation of cytotoxic T cells to occur without stimulation from TH1 cells, the activation is not as effective or long-lasting.
Once activated, cytotoxic T cells serve as the effector cells of cellular immunity, recognizing and kill cells infected with intracellular pathogens through a mechanism very similar to that of NK cells. However, whereas NK cells recognize nonspecific signals of cell stress or abnormality, cytotoxic T cells recognize infected cells through antigen presentation of pathogen-specific epitopes associated with MHC I. Once an infected cell is recognized, the TCR of the cytotoxic T cell binds to the epitope and releases perforin and granzymes that destroy the infected cell (Figure \(\PageIndex{6}\)). Perforin is a protein that creates pores in the target cell, and granzymes are proteases that enter the pores and induce apoptosis. This mechanism of programmed cell death is a controlled and efficient means of destroying and removing infected cells without releasing the pathogens inside to infect neighboring cells, as might occur if the infected cells were simply lysed.
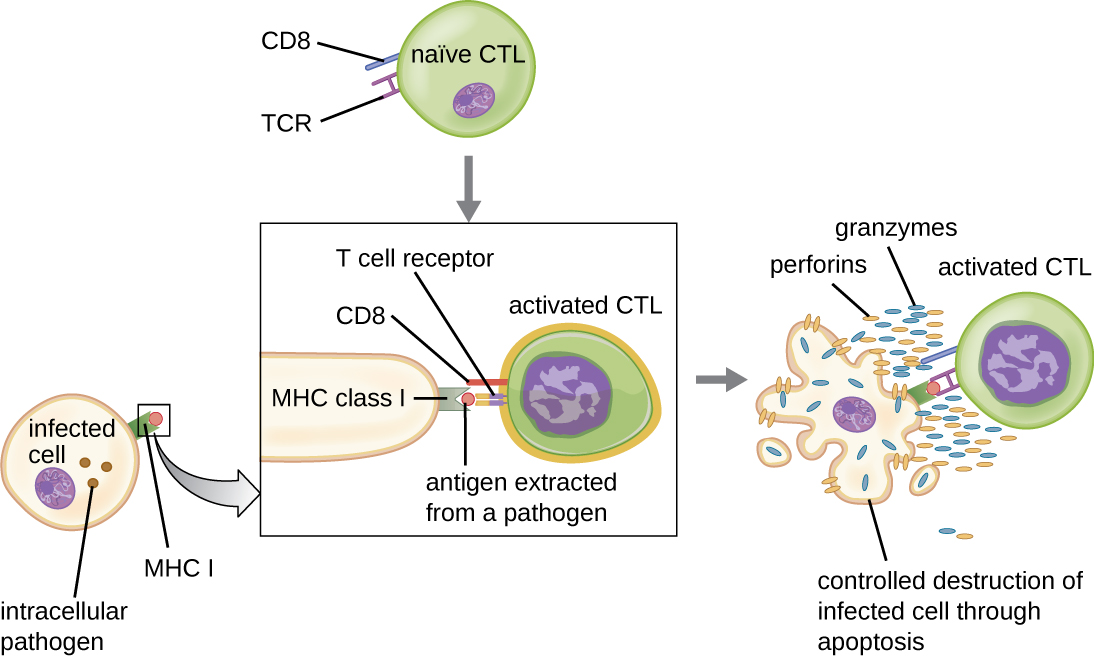
In this video, you can see a cytotoxic T cell inducing apoptosis in a target cell.
- Compare and contrast the activation of helper T cells and cytotoxic T cells.
- What are the different functions of helper T cell subtypes?
- What is the mechanism of CTL-mediated destruction of infected cells?
Superantigens and Unregulated Activation of T Cells
When T cell activation is controlled and regulated, the result is a protective response that is effective in combating infections. However, if T cell activation is unregulated and excessive, the result can be a life-threatening. Certain bacterial and viral pathogens produce toxins known as superantigens (see Virulence Factors of Bacterial and Viral Pathogens) that can trigger such an unregulated response. Known bacterial superantigens include toxic shock syndrome toxin (TSST), staphylococcal enterotoxins, streptococcal pyrogenic toxins, streptococcal superantigen, and the streptococcal mitogenic exotoxin. Viruses known to produce superantigens include Epstein-Barr virus (human herpesvirus 4), cytomegalovirus (human herpesvirus 5), and others.
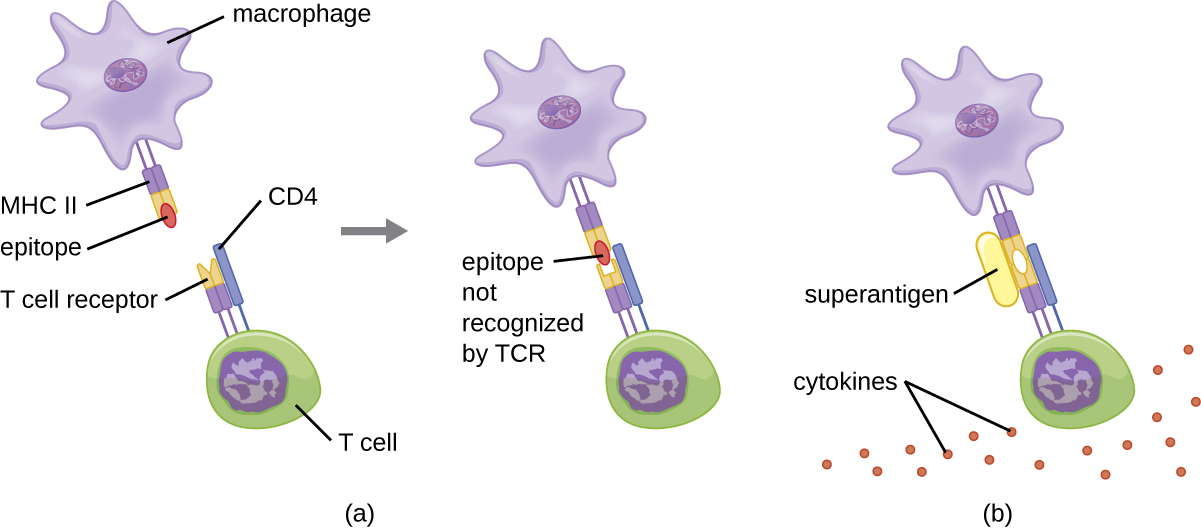
The mechanism of T cell activation by superantigens involves their simultaneous binding to MHC II molecules of APCs and the variable region of the TCR β chain. This binding occurs outside of the antigen-binding cleft of MHC II, so the superantigen will bridge together and activate MHC II and TCR without specific foreign epitope recognition (Figure \(\PageIndex{7}\)). The result is an excessive, uncontrolled release of cytokines, often called a cytokine storm, which stimulates an excessive inflammatory response. This can lead to a dangerous decrease in blood pressure, shock, multi-organ failure, and potentially, death.
- What are examples of superantigens?
- How does a superantigen activate a helper T cell?
- What effect does a superantigen have on a T cell?
Melissa, an otherwise healthy 22-year-old woman, is brought to the emergency room by her concerned boyfriend. She complains of a sudden onset of high fever, vomiting, diarrhea, and muscle aches. In her initial interview, she tells the attending physician that she is on hormonal birth control and also is two days into the menstruation portion of her cycle. She is on no other medications and is not abusing any drugs or alcohol. She is not a smoker. She is not diabetic and does not currently have an infection of any kind to her knowledge.
While waiting in the emergency room, Melissa’s blood pressure begins to drop dramatically and her mental state deteriorates to general confusion. The physician believes she is likely suffering from toxic shock syndrome (TSS). TSS is caused by the toxin TSST-1, a superantigen associated with Staphylococcus aureus, and improper tampon use is a common cause of infections leading to TSS. The superantigen inappropriately stimulates widespread T cell activation and excessive cytokine release, resulting in a massive and systemic inflammatory response that can be fatal.
Vaginal or cervical swabs may be taken to confirm the presence of the microbe, but these tests are not critical to perform based on Melissa’s symptoms and medical history. The physician prescribes rehydration, supportive therapy, and antibiotics to stem the bacterial infection. She also prescribes drugs to increase Melissa’s blood pressure. Melissa spends three days in the hospital undergoing treatment; in addition, her kidney function is monitored because of the high risk of kidney failure associated with TSS. After 72 hours, Melissa is well enough to be discharged to continue her recovery at home.
In what way would antibiotic therapy help to combat a superantigen?
Key Concepts and Summary
- Immature T lymphocytes are produced in the red bone marrow and travel to the thymus for maturation.
- Thymic selection is a three-step process of negative and positive selection that determines which T cells will mature and exit the thymus into the peripheral bloodstream.
- Central tolerance involves negative selection of self-reactive T cells in the thymus, and peripheral toleranceinvolves anergy and regulatory T cells that prevent self-reactive immune responses and autoimmunity.
- The TCR is similar in structure to immunoglobulins, but less complex. Millions of unique epitope-binding TCRs are encoded through a process of genetic rearrangement of V, D, and J gene segments.
- T cells can be divided into three classes—helper T cells, cytotoxic T cells, and regulatory T cells—based on their expression of CD4 or CD8, the MHC molecules with which they interact for activation, and their respective functions.
- Activated helper T cells differentiate into TH1, TH2, TH17, or memory T cell subtypes. Differentiation is directed by the specific cytokines to which they are exposed. TH1, TH2, and TH17 perform different functions related to stimulation of adaptive and innate immune defenses. Memory T cells are long-lived cells that can respond quickly to secondary exposures.
- Once activated, cytotoxic T cells target and kill cells infected with intracellular pathogens. Killing requires recognition of specific pathogen epitopes presented on the cell surface using MHC I molecules. Killing is mediated by perforin and granzymes that induce apoptosis.
- Superantigens are bacterial or viral proteins that cause a nonspecific activation of helper T cells, leading to an excessive release of cytokines (cytokine storm) and a systemic, potentially fatal inflammatory response.
Footnotes
- 1 Blaschitz C., Raffatellu M. “Th17 cytokines and the gut mucosal barrier.” J Clin Immunol. 2010 Mar; 30(2):196-203. doi: 10.1007/s10875-010-9368-7.


